A host of popular Android apps from a major Chinese developer, including a selfie app with more than 50 million downloads, have been com...
A host of popular Android apps from a major Chinese developer, including a selfie app with more than 50 million downloads, have been committing large-scale ad fraud and abusing user permissions, a BuzzFeed News investigation of popular Android apps has found. In several cases, the apps took steps that concealed their connections to the developer, DU Group, to users and failed to clearly disclose they were collecting and sending data to China. The investigation also raises questions about Google's policing of apps in the Play store for fraud and data collection practices.
DU Group is a Chinese app developer that claims more than 1 billion users worldwide, and was spun off from Baidu, one of China’s largest tech companies, last year. At least six of DU Group’s apps, which together have more than 90 million downloads from the Google Play store, have been fraudulently clicking on ads to generate revenue, and at least two of them contain code that could be used to engage in a different form of ad fraud, according to findings from security and ad fraud researchers Check Point and Method Media Intelligence.
The DU Group apps were identified after BuzzFeed News gathered a list of close to 5,000 popular apps from the Google Play store, along with associated information, such as the developer’s name, number of installs, and requested permissions. Apps that asked for a suspiciously large number of user permissions, or permissions deemed potentially “dangerous” by Android, were provided to researchers at several data analysis and security firms. (For a more detailed description of the methodology, see the bottom of this article.)
The problem isn’t limited to DU Group, however. Other Android apps with a high number of unnecessary permissions identified by BuzzFeed News include a hugely popular TV remote app that says it might use a phone’s microphone to record sound while a user watches TV, a Chinese-language kids app that sent personal information without any encryption to servers in China, and a flashlight app that took dozens of unnecessary and potentially invasive permissions.
The findings demonstrate how Google’s Play store, the largest app store in the world, has been exploited by developers who easily conceal who they are from users, offer apps with invasive permissions, and use these permissions to commit ad fraud — all while collecting huge amounts of user data. The result is an app ecosystem that’s easily taken advantage of to abuse users and steal money from advertisers.
Google told BuzzFeed News that it has blacklisted the six DU Group apps found committing ad fraud. This means they can no longer use any of Google’s ad products to earn money.
“We explicitly prohibit ad fraud and service abuse on Google Play. Developers are required to disclose the collection of personal data, and only use permissions that are needed to deliver the features within the app,” a company spokesperson said in an emailed statement. “If an app violates our policies, we take action that can include banning a developer from being able to publish on Play.”
The DU apps in question also violate the Play store policy against apps that “misrepresent or conceal their ownership,” given that they do not disclose any connection to DU Group to users.
After initially stating that the apps in question would remain in its store while it investigated, shortly before this article's publication a Google spokesperson confirmed they have now been removed. The company would not say if it plans to take action against DU Group overall.
The day before Google responded to BuzzFeed News’ questions about app permissions and developers concealing their identity, the company also published a blog postoutlining a new approach to user permissions and measures “to prevent bad-faith developers from gaming our systems.” It said it will be hiring more people to evaluate apps for the Play store.
DU Group did not respond to multiple emails requesting comment.
Richard Kramer, a senior analyst of Arete Research, told BuzzFeed News Google isn’t doing enough to protect users.
“You cannot separate the behaviour of DU — spun out of Baidu a year ago, in which they still own 34% — from the US-listed parent,” he said in an email. “Ad fraud is simply the norm in China (and for many other apps), and ... Google should be doing far more to prevent it, even if it would materially reduce sales. They cannot claim ignorance of, or deny the problem.”
DU Group’s ad fraud follows on previous BuzzFeed News reporting that revealed two other prominent Chinese Android app developers, Cheetah Mobile and Kika Tech, were abusing user permissions to engage in ad fraud.
In response to that investigation, Sen. Mark Warner of Virginia said Chinese mobile app companies pose a national security risk due to their voracious data collection and Chinese laws that make them “ultimately beholden to the Communist Party.”
“All this information is ending back up in data repositories in China. Beyond the [ad] fraud, just all the personal information that is being collected on Americans” is a problem, he said.
Grant Simmons, the head of client analytics for the app analysis and attribution company Kochava, said the behaviors identified in this investigation often occur in the background when a user isn’t using the app in question. He compared it to “having downloaded an app that operates as a Trojan horse for the purposes of data collection.”
“End users are not aware of how data is generated by the apps they use — and how frequently the data generated is used for ad fraud or further privacy violations,” he said.
A review of app privacy policies by Privacy International found many identified in this research were confusing or inadequate, and raised questions about when they share data with government authorities and other third parties.
“Beyond questions of legal compliance, companies need to stop exploiting people’s data,” said Frederike Kaltheuner, the data program lead of Privacy International. “What happens to your data matters, because it can be used against you or for purposes that you fundamentally disagree with. At the moment you often have to [be] an expert to understand what happens to your data — with whom it’s shared, sold, and by whom it’s exploited. That’s a huge problem.”
A family of apps committing ad fraud
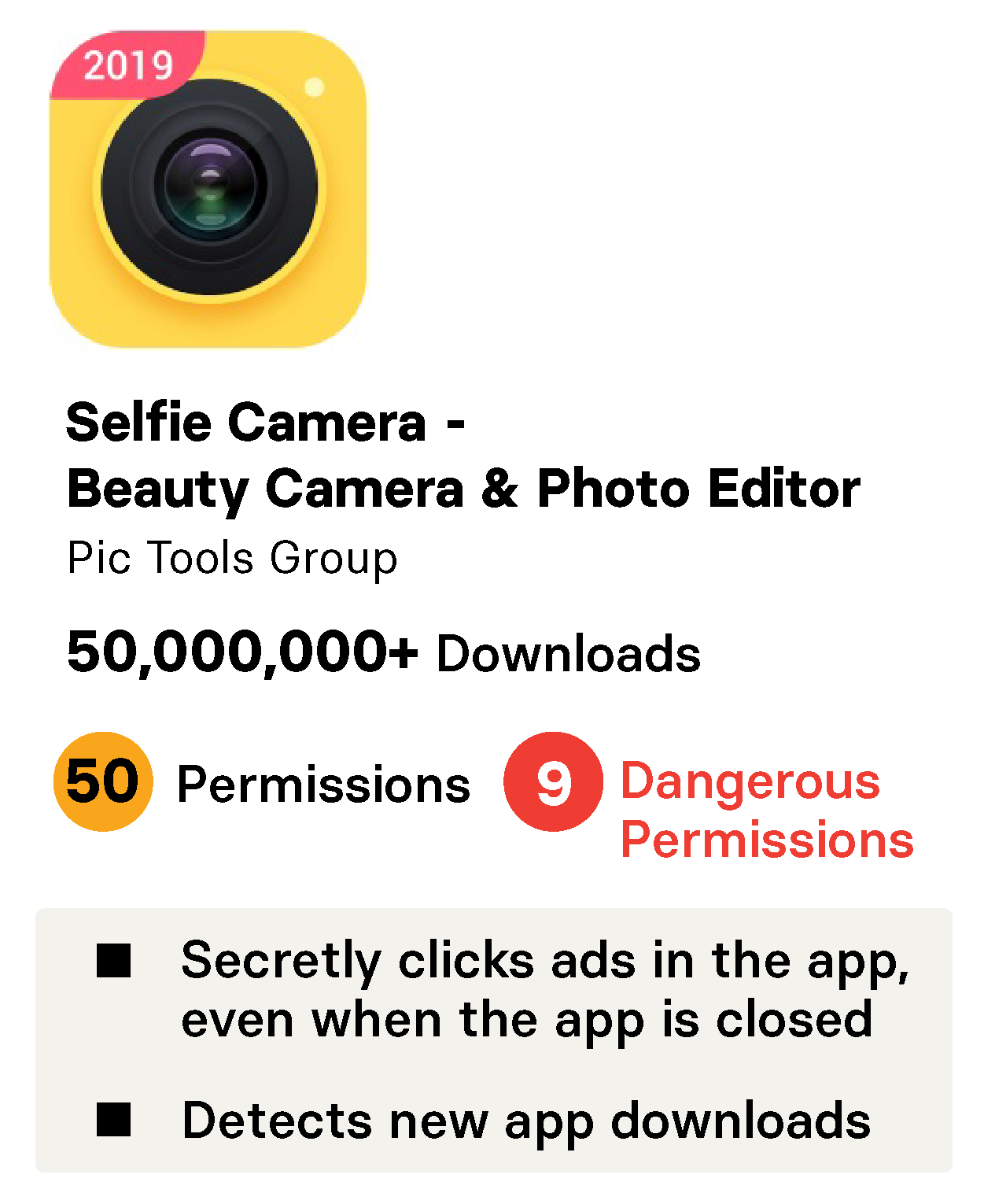
The Selfie Camera app had been installed more than 50 million times from the Google Play store, and maintained a 4.5-star rating after tens of thousands of reviews. In 2017, Google listed it as one of the most popular new apps in the UK. Those stats made it seem like a safe bet for users, but three different researchers found problems with the app that make it a risk to download.
Most alarmingly, Check Point found the app contains code that causes it to fraudulently click on ads in the app without the user’s knowledge. The company’s researchers documented fake clicks taking place with ads served by AdMob and MoPub, the mobile ad networks operated by Google and Twitter, respectively. (MoPub and Twitter did not respond to a request for comment.)
The fraudulent clicks even occur when the app isn’t open, which can drain a phone’s battery and consume data, according to Aviran Hazum, the analysis and response team leader for Check Point.
His team documented the app “checking if [a] user hasn’t clicked on an ad yet [and then] clicking at random intervals” on ads to generate fraudulent revenue.
“It’s not something you can say is in the gray area — it's a clear-cut fraudulent activity,” he told BuzzFeed News.
Selfie Camera is one of six apps owned by DU Group that Check Point found engaged in fake ad clicking. The other apps were Omni Cleaner, RAM Master, Smart Cooler, Total Cleaner, and AIO Flashlight. They had been installed more than 40 million times from the Google Play store prior to being removed.

BuzzFeed News
Google said this form of “click fraud” is rare and against its policies, which is why it blacklisted all six apps from its ad products. The company pointed to a recent blog postabout action it took in 2018 against malicious ads and actors.
Along with committing ad fraud, the apps also concealed their connection to DU Group from users. In Google’s Play store, all of the above apps (except for AIO Flashlight) list their developer as “Pic Tools Group (Photo Editor& Photo Grid&Collage).” There are no references to DU Group, or Baidu, on the apps' descriptions within the store.
“It provides a layer of obscurity for the user,” Hazum said.
BuzzFeed News
Google’s developer policy does not allow “apps or developer accounts that impersonate any person or organization, or that misrepresent or conceal their ownership or primary purpose ... or conceal their country of origin and that direct content at users in another country.”
Of all the above apps, Selfie Camera raised the most concerns among researchers. In addition to the fake clicks documented by Check Point, Method Media Intelligence identified code in the app that could enable app attribution ad fraud. Praneet Sharma of MMI said, “There is a clear pattern of using certain packages that game install attribution and ad calls,” and warned of the “immense and dangerous amount of permissions” in this and other apps he examined. (Sharma did not see the app committing attribution ad fraud.)
Attribution ad fraud, which BuzzFeed News previously reported was committed by Cheetah Mobile and Kika Tech, is used to falsely claim credit for app installations. Developers often pay a “bounty” to partners who help drive new installations of their products. In this case the selfie app from DU Group contained code enabling it to detect when someone downloaded a new app to their phone, and could be used to help claim any bounty on an offer.
Beyond the ad fraud activity, the app also comes bundled with unrelated — and undisclosed — features, documented in user complaints on Play store reviews and an analysis by Eset, a security firm.
“Completely false advertisement ... it has a bunch of hidden ‘performance enhancements’ for my phone that only screw it up more. I'll be reporting this as it needs to be in the description,” read a recent review from Duncan Mugume, a user in Uganda who told BuzzFeed News he downloaded the app after seeing an online ad for it.
He said in a Facebook message that after he installed the app it “behaved completely different” than expected, including running “scans” of his phone while it was not in use.
Lukas Stefanko, a malware researcher with Eset, examined the app for BuzzFeed News and found it contains a wide range of functionality not revealed to the user in the Play store, including a hidden battery monitor, CPU cooler, and the ability to view external websites, among others.
Stefanko said this extra functionality adds vulnerabilities because the app could be used to load malicious links. (He did not witness any such activity.)
One puzzling behavior by many of DU Group’s unbranded apps is that their privacy policies werere hosted on Tumblr blogs with strange names. Selfie Camera hosts its policy at dreamilyswimmingwizard.tumblr.com while other apps have policies at yesexactlyinnerbouquetstuff.tumblr.com/ and superiorzzr.tumblr.com.
These policies don’t reveal that the user’s data is being collected by DU Global, adding yet another layer of obfuscation. Kaltheuner, of Privacy International, told BuzzFeed News the policies are vague about how third parties, including potentially the Chinese government or other authorities, can gain access to the data being collected. She also said the policy for Selfie Camera incorrectly claims it does not collect personal data. Under GDPR, the European data legislation, a device ID is considered personal data, and Selfie Camera collects this from users.
One DU Group app that is explicit about user data being sent to China is the Meet chat app. Like others, it does not list DU Group anywhere on its Play store listing. But it says in its privacy policy that “it may require us to transfer your Personal Data to countries outside of the European Economic Area ... including to countries such as the People’s Republic of China or Singapore.” (The researchers did not identify any ad fraud taking place in Meet.)
DU Group did not respond to multiple requests for comment.
Flashlight apps taking permissions, engaging in ad fraud
Almost all Android phones ship with a built-in flashlight, making these apps largely unnecessary. Yet many third-party lights boast millions of installs, and have in the past been used as a Trojan horse to deliver malware or engage in ad fraud by loading ads in the background without a user’s knowledge. BuzzFeed News’ investigation identified multiple flashlight apps that requested a suspiciously high number of permissions from users, and/or were engaged in ad fraud.
“[Flashlight app developers] took advantage of a window of opportunity when iPhones and Android devices did not have built-in flashlight functionality, so real humans downloaded flashlight apps that asked for insane permissions and few noticed since they just gave all permissions when installing,” Augustine Fou, an independent ad fraud researcher, told BuzzFeed News.
BuzzFeed News
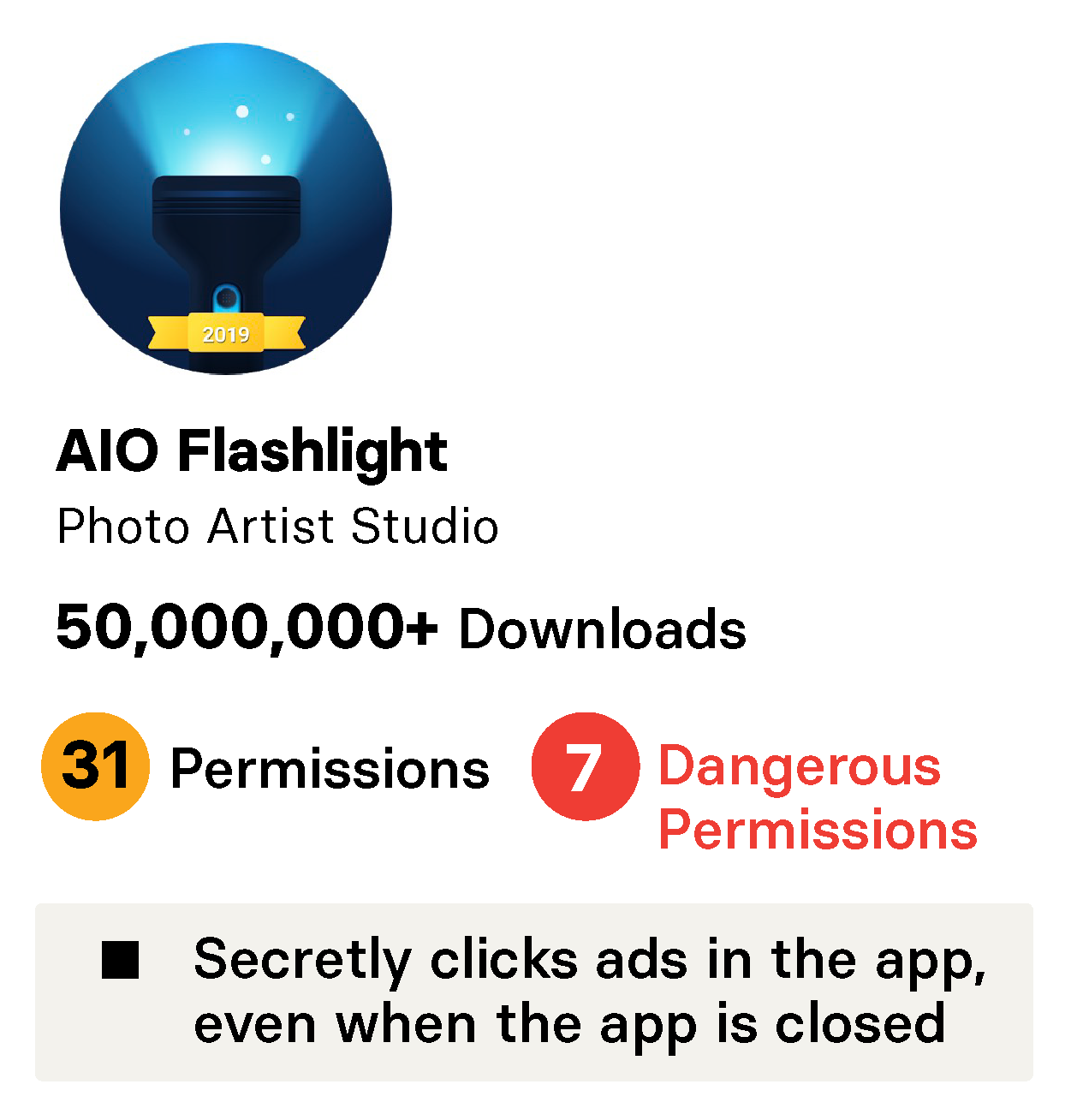
As previously noted, the AIO Flashlight from DU Group was part of the group of apps fraudulently clicking on ads. It also took 31 permissions, seven of which are in the dangerous group. The Emoji Flashlight, from APUS Apps of China, has over 5 million installs and took 30 permissions, of which seven are in the dangerous group — far more than are needed to function. How many permissions does a flashlight app actually need? This app in the Play store took just two permissions and does the job.
A request for comment sent to the email address listed on the Emoji Flashlight’s Play store page did not receive a reply. Emails to APUS Apps also went unanswered.
A TV remote that says it might use your phone mic to record what you watch
While the most invasive apps identified in the investigation belonged to Chinese companies, one American-made app stood out for its dragnet data collection policy and high number of permissions.
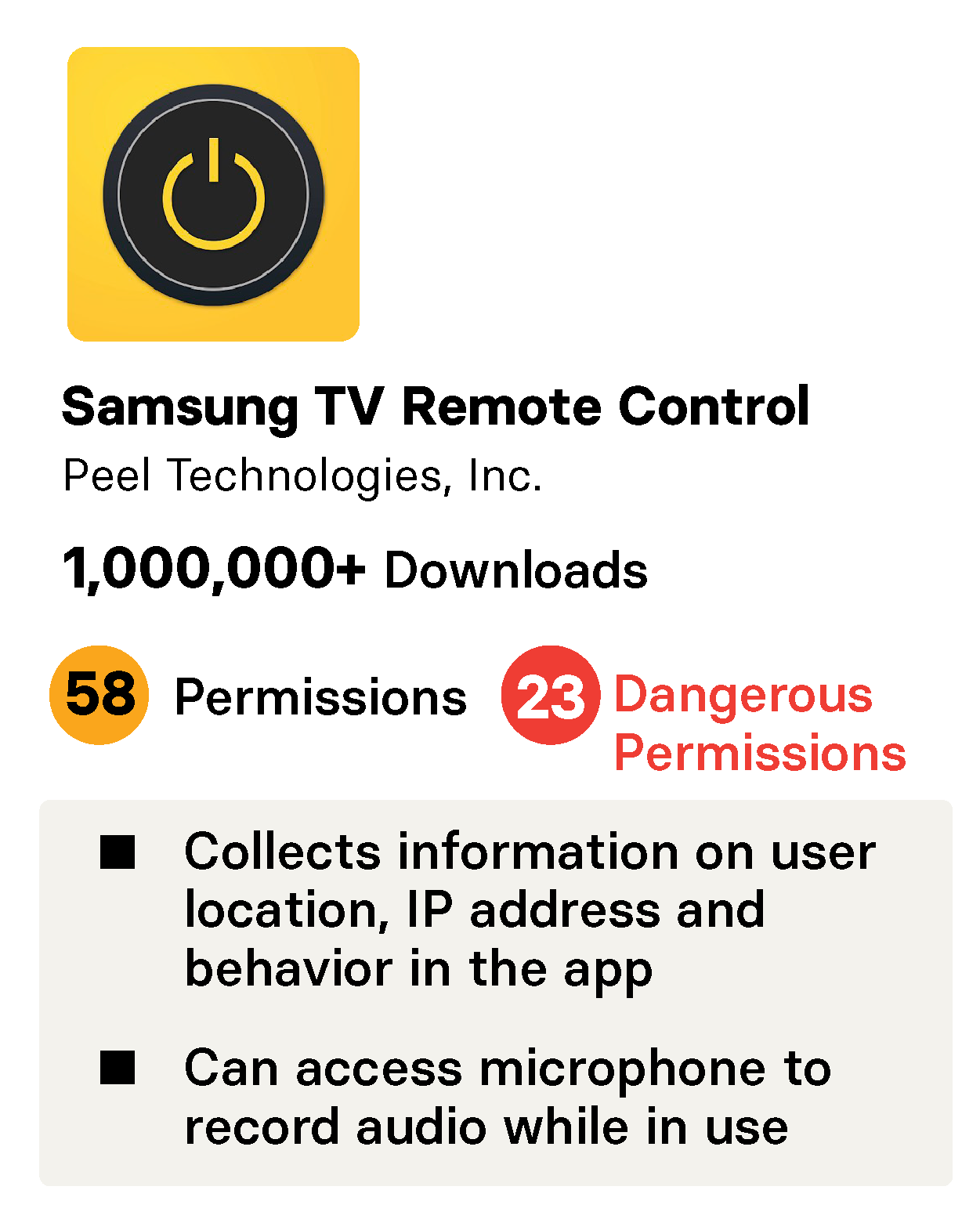
The Samsung TV Remote Control app from Peel Technologies took 58 permissions, 23 of which are in the dangerous category defined by Android. The app is one of a family of TV remote applications from Peel that have similar functionality and permissions. They are all covered by a single privacy policy that says the app collects detailed information about the “content you consume (validated by audio content recognition).” This suggests the app accesses the microphone to record audio while you use it. It also collects information on your location, IP address, device, and behavior when you use the app.
In an email response, Peel said its apps do not perform audio content recognition, but did not respond to a follow-up question about why that feature is cited in its privacy policy. It also said it only shares “Non-Personally Identifiable Location data for a fraction of our users” with third parties.
While it may not be a household name, the company is a global player. It has claimed a registered user base of more than 130 million people and raised more than $86 million in venture capital funding. (Its most recent round of financing came in 2014 and was led by Chinese e-commerce and tech conglomerate Alibaba Group.)
BuzzFeed News
One reason it has attracted so many users over its history is because in 2012 Peel signed a deal to preinstall its apps on some Samsung phones. (It had a similar deal with handset maker HTC.)
Patrick Flynn, a management consultant in Brisbane, Australia, told BuzzFeed News that his Samsung Galaxy, purchased around 2015, came with a Peel remote app preinstalled. He recently became frustrated after the app kept taking over his screen with ads. The same happened to his mother-in-law, who also owns a Samsung Galaxy.
That behavior was documented earlier this year by mobile security firm Wandera, which called out the Peel remote for “misusing permissions functionality and aggressively advertising to its users.” Peel initially said its apps “do not do any advertisements at the moment.” However, BuzzFeed News found at least four of its apps were offering inventory for advertisers to buy across several ad networks. The company then said it’s running “minor experiments running to find the right balance between interstitial [ads] and user churn.”
Flynn was so frustrated by the adds that he tried to delete the app from his phone. But it kept reappearing.
“When it came back, covering up our lock screens again, I was very frustrated,” he said. Flynn had to search online to find out how to disable the app and its many permissions.
“I've since gone through, revoked all permissions, disabled auto updates,” he said. “The whole experience has put me off Samsung altogether. It's still there, and that annoys me.”
“But when it made life harder for an older lady who really struggles with technology, I was angry,” he said. “I've had an easier time removing viruses.”
He posted a review about his struggles in the Play store earlier this year to warn other users.
Peel told BuzzFeed News its apps are no longer preinstalled on Samsung or HTC phones. Samsung did not respond to a request for comment, though the company continues to maintain an online help page dedicated to telling people how to disable the Peel TV remote app.
A kids app sending personal data in the clear
Finally, one kids app stood out among the apps that took unnecessary permissions. The WaWaYaYa app is a reading app for kids that offers Chinese-language content. It also took 32 permissions, seven of which are from the dangerous group. Most alarmingly, analysis from Stefanko of Eset found the app is sending user information such as an email, username, real name, and information about their device back to servers in China without encryption or other protection measures.
The app is only available in Chinese and has only been installed 1,000 times from the Play store. The developer of the app did not reply to a request for comment. ●
How we found the apps and analyzed them
In February, BuzzFeed News collected information from the US Google Play store on the top 600 free, paid, and highest-grossing Android apps in four categories: overall, games, kids apps, and tools. Some apps appeared in multiple lists (i.e., both top-grossing games and top-grossing overall); in total, BuzzFeed News identified 4,880 apps.
Among the data that can be gleaned from the Play store are each app’s permissions. BuzzFeed News cross-referenced those permissions with Android’s official documentation, which assigns certain permissions a “protection level” of “dangerous.” Such permissions tend to be those that provide access to sensitive information (text messages, body sensors, location, etc.) or those that have the ability to exert effects outside of the app (sending text messages, modifying contacts, creating voicemails, etc.).
BuzzFeed News manually identified apps that requested a high number of permissions, including those assigned as “dangerous,” and began researching those that took more permissions than appeared to be required for them to function (such as flashlight apps). Apps that warranted technical examination were provided to Check Point, Method Media Intelligence, and Eset for further analysis.